SMS has more reach than other messaging channels because you don’t need a smartphone and an internet connection to access a text message.
But what gives SMS marketing its power is the engagement it generates.
While email has a 20 to 30 percent open rate, SMS has a 98 percent open-rate. And 90 percent of recipients read their text messages within three seconds of receiving them.
More so, SMS has a reply rate as high as 45 percent, and an average person responds to an SMS within 90 seconds.
What’s more?
SMS marketing generates outsized ROI. For example, a British motor racing circuit earned a 680 percent return on their SMS marketing efforts.
How can you benefit from all these goodies?
Let’s explore how you can leverage SMS to boost your profits, earn buyers’ trust, and gain referrals.
Table of Contents: 14 Ways Savvy Brands Use SMS to Earn More Money, Trust, and Referrals
You may skip to any part of this content by clicking any of the items on the list.
-
- Build a Loyalty Program by Leveraging SMS
- Build Referrals from Loyal Buyers
- Boost Your Subscriber Base by Targeting In-Store Shoppers
- Track and Measure Your Customer Engagement Levels
- Use SMS for Call to Action
- Manage Your Product Recalls and Returns
- Use SMS to Boost Your Email Open-Rate
- Offer Discounts and Build Top-of-the-Mind Awareness
- Boost Your Revenues By Getting Instant Buyer-Feedback
- Abandoned Cart Notification
- Delivery Alert and Customer Service
- Product Launch, New Stock, and Product Updates
- Manager Your Customer Appointments
- Distribute Your Coupon to More People
1. Build a Loyalty Program by Leveraging SMS
More businesses are favoring customer retention over acquisition. Specifically, businesses favoring customer retention over acquisition moved from 70 percent to 80 percent in one year.
One study showed that 82 percent of shoppers choose businesses that have loyalty programs over others. And loyalty programs guarantee customer retention.
Fortunately, raising your customer retention rate by five percent is a big deal. It could earn your business up to 125 percent more profit.
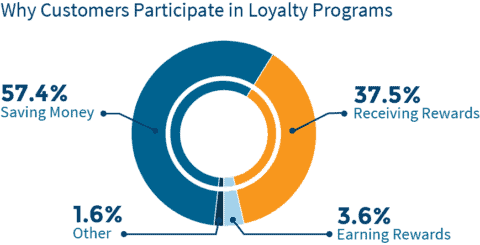
Image Credit: TechnologyAdvice
So it only makes sense for businesses to gravitate towards customer loyalty strategies. But some businesses are better at using potent tactics than others.
Savvy brands understand the power of SMS, and they’re using it to drive their customer loyalty growth at the speed of thought.
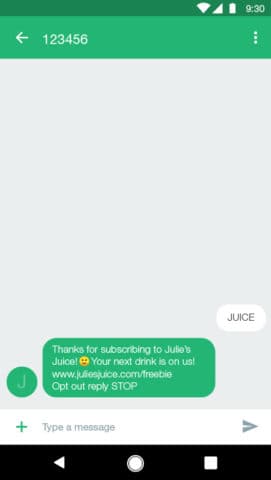
Image Credit: Wikimedia Commons
When shoppers buy from them, they seize that moment. These brands would send buyers an SMS invite to join their loyalty programs in exchange for intelligently structured benefits.
2. Build Referrals from Loyal Buyers
Loyal customers are happy to introduce you to new customers, or they’re willing to introduce new people to your business.
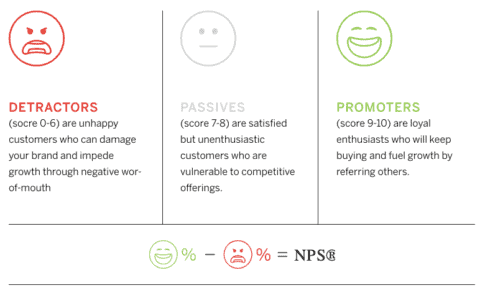
Your customers’ willingness to introduce their friends to your business is a Net Promoter Score (NPS) booster.
If the term is new to you, your business’s NPS shows you the level of loyalty your customers have for the business. It shows you how likely they’ll recommend your product or service to their friends or colleagues.
On a scale of one to ten:
- 9 – 10 are loyal, would recommend you to others, and would keep buying
- 7 – 8 are indifferent and can move to other brands if they want
- 0 – 6 are unhappy and can soil your reputation with negative comments
In a Bain and Company study, shoppers who’ve bought ten or more times from you refer 50 percent more buyers than one-time shoppers.
So the best audience to target for your referral programs is frequent buyers.
Regular shoppers are more likely to refer people to your business. And they send significantly more leads your way than anyone else.
Using SMS, which almost guarantees high open rates, ask your loyal buyers to refer people to your business. You may decide to incentivize this request for referrals too.
3. Boost Your Subscriber Base by Targeting In-Store Shoppers
The line separating the online and offline world is quickly blurring out. And this isn’t only about virtual or augmented reality. Even the simple mobile phone has become instrumental in bringing your local store online.
Use attractive offers in your retail shops to ask your in-store shoppers to subscribe via SMS in exchange for incentives. You can offer different discount types, depending on your strategy. For instance, asking your customers to subscribe using a short code by SMS for a credit card.
4. Track and Measure Your Customer Engagement
SMS marketing is a business growth strategy that helps you engage your customers. As you might imagine, engaged customers buy more from you.
Hence, you can measure the success rate of your marketing campaign by sending messages with trackable links. These types of messages make it easy to track your customers’ engagement with your marketing messages.
Return to the Table Of Contents
5. Use SMS for Call to Action

Since the click-through rate (CTR) is high with SMS, leverage it to deliver timely messages to your audience.
However, not all Call to Action (CTA) is appropriate for SMS. With a maximum of 160 characters, your SMS can’t have lengthy texts that end with “Read More,” or pitches that end with “Buy Now” or “Sign Up.”
However, your timely messages can use:
- Click the link
- Call us
- Text back
- Visit us
Yes, that sort of thing. You want them to act.
6. Manage Your Product Recalls and Returns
Defective products can impact your reputation negatively. Hence, as an obligation, you must recall hazardous products that result from design and production errors.
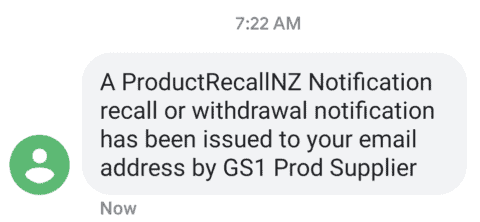
Image Credit: GS1 New Zealand
You want to act speedily when notifications of product defects reach you. And an SMS platform can help. You can use text messages to manage single product defects to mass defects.
Leveraging SMS, you can quickly reach your customers with information on the status of your product, and guide them on the next course of action.
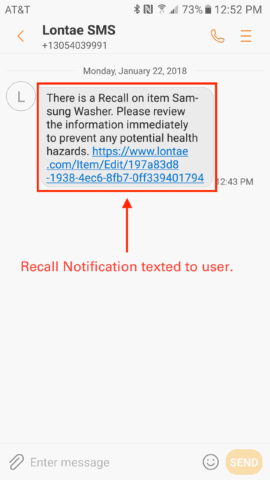
Image Credit: Lontae
For mass defects, your first call would be to stop all distribution of the product, then send recall notification to your customers through SMS.
7. Use SMS to Boost Your Email Open-Rate
Some businesses either use Email or SMS in their marketing campaign, but savvy ones use both channels strategically.
Since emails convey detailed messages well, you can use it for lengthy conversations that require explanations. Furthermore, an email allows attachments like brochures and downloadable documents. But the chances are that most of your customers won’t see the email.
Hence, you want to leverage the higher open rate of text messaging to boost your email open-rate.
In one Smart Insights report, SMS helped businesses experience a 20 to 30 percent boost in their email open. A simple message that asked eads, “have you read our email?” did the magic.
8. Offer Discounts and Build Top-of-the-Mind Awareness
Building your brand takes more than having a catchphrase, brilliant logo designs, and brand colors. You want your customers to remember you.
To stay top-of-the-mind, you can use SMS strategies like
- Keeping track of and sending anniversary messages to your customers
- Sending them tips and helpful information on using your product or service
- Offering discounts and promotions
- Giving them party invites
- Sharing news headlines if appropriate
And more. Here are some examples.
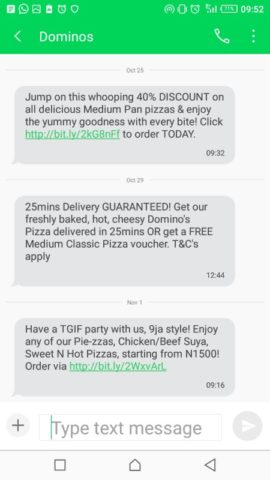
A local Domino’s Pizza stays top-of-the-mind by offering discounts via text messages.
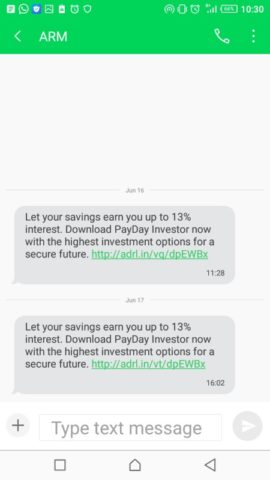
Another brand, ARM, also uses discounts sent via SMS to invite their leads to sign up for their program.
You may also use trackable URLs in your SMS to uncover the best send times for your messages. And then take advantage of the timing when running your campaign.
Up to 90 percent of your customers would read your message. So if you’re offering discounts, you want to be ready for the rush. For example, make sure your staff can fulfill your offers on time.
9. Boost Your Revenues By Getting Instant Buyer-Feedback
Sending your buyers a survey immediately they leave your store can help you get a sense of how satisfied they feel about your food or their shopping experience at your place.
This point can also be helpful for an event if you host online or offline events. When a session ends, get a quick sense of what your attendees enjoyed and what they didn’t like. And then, use that feedback to improve on your coming event sessions.
You can send your leads to a page on your website or app to leave a short survey like the one below.
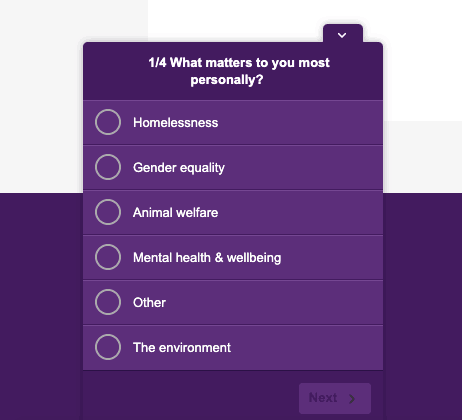
Surveys and feedback can help you discover profitable patterns you can leverage to boost your revenue and customer satisfaction.
10. Abandoned Cart Notification

Trying to recover all abandoned carts is a waste of time because, on average, approximately 70 percent of shopping carts are abandoned. As high as 92 percent of the visitors to a retail website have no intention to buy.
You can automate your SMS such that when a customer adds products to their cart without checking out, they receive notification automatically. But you must have collected their phone numbers to make this possible. You must send the abandoned cart SMS fast and create an easy link for them to get back to the cart.
You can increase your success rate by offering incentives, such as discounts and free deliveries.
11. Delivery Alert and Customer Service
Customers want you to keep them in the loop. So you could send them delivery tracking notifications about their purchases by SMS.
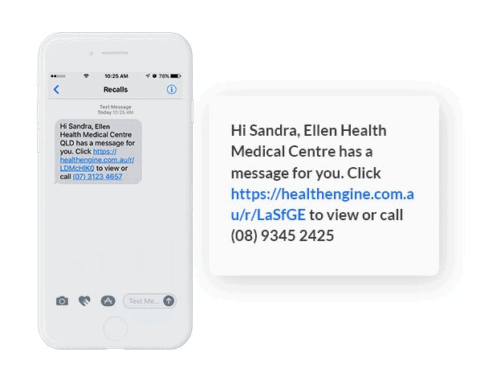
More so, you can use SMS for customer service. This Australian health care service does with their patients, see the message above.
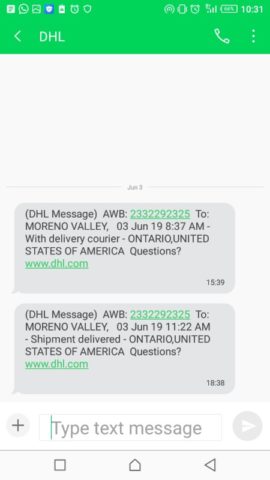
Brands like Amazon and DHL already use this channel because it’s effective. You can copy them safely.
12. Product Launch, New Stock, and Product Updates

Most businesses have come to rely on email for their product launch and for keeping their customers updated about new stocks or improvements. But SMS can offer exciting opportunities too.
You can inform your target audience about new products, discounts, services, and events via text messages. Studies have shown that SMS might even be more potent than email.
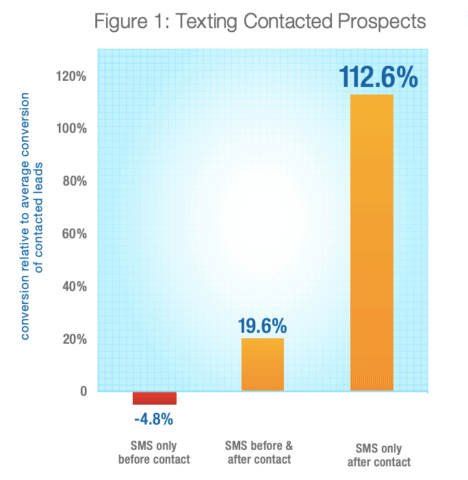
SMS messages have a 209 percent higher response rate than messages on apps, email, or Facebook. In one study, sales leads who got a text message during a product launch converted 40 percent higher than those who didn’t get a text message.
Salesforce says that 89 percent of marketers report that SMS marketing commands more results than business websites and display ads. More so, 82 percent of marketers either maintained or increased their investment in SMS marketing.
In short, using SMS to launch your product gets you the types of results you love.
13. Manage Your Customer Appointments

If you offer services, you might want to confirm or remind your customers of an appointment via SMS. You’d reduce the chances of cancellation because 70 percent of respondents agree that using SMS is a good way to get their attention.
Likewise, if you choose to stay open to accommodate late buyers, you can inform your busy customers of extended hours.
14. Distribute Your Coupon to More People

Text messages can create a sense of urgency around your discount, coupon codes, or flash sales. Due to the fast open and response rates of SMS, you can get a response almost instantly.
So you can compile the phone numbers of leads who respond and target them in future campaigns.
Mobile coupons allow you to send your brand codes to customers quickly. You can send them as coupon codes via SMS that they can present at check out.
Get Savvy: Earn More Money, Trust, and Referrals
It’s action time. But you don’t have to act on everything. Take one or a few ideas that resonate with you. And put them to work. That’s what works.
Decide on what goals matter most to your business right now. Is earning more money the most import thing right now? Would earning more trust boost your business value better? Or would you rather get more referrals now?
It’s time to get savvy. Choose a goal and take action today.