For businesses and users alike, there has recently been a big security shift to two-factor authentication, and many companies are leaning on mobile devices to provide authentication codes in a timely manner for users.
The way it works is pretty simply. Once customers login using their usernames and passwords, they have to then authenticate their entry a second time by entering a code sent to their mobile device.
Companies all around the globe also rely on SMS for redundancy in communication when internet isn’t available, to ensure their communications are never disrupted.
With a lot of services relying on this method of authentication and redundancy, there has never been more pressure on you mobile accounts to stay secure. It’s important to make sure your SMS carrier isn’t the weakest link in your security chain by choosing a secure SMS gateway solution.
Why rely on SMS in the first place? Your information is valuable.
The number one method of communication is email—personal and business users alike across the web use it to communicate, as well as to authenticate accounts and send sensitive information.
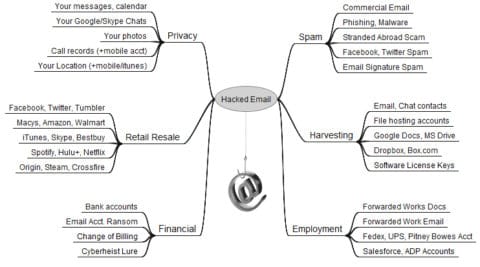
This infographic from Krebson Security shows just how valuable your email account can be when hacked—pretty much all of your accounts are connected to your email, and it can be a little scary to realize what someone could access there:
Krebson also goes into detail about how valuable these account can be to a hacker:
“One prominent credential seller in the underground peddles iTunes accounts for $8, and Fedex.com, Continental.com and United.com accounts for USD $6. Groupon.com accounts fetch $5, while $4 buys hacked credentials at registrar and hosting provider Godaddy.com, as well as wireless providers Att.com, Sprint.com, Verizonwireless.com, and Tmobile.com. Active accounts at Facebook and Twitter retail for just $2.50 a piece.”
In addition to the monetary value, hackers are also disrupting businesses with security breaches, account turnovers and major customer data thefts. If your internet security fails, you’re vulnerable to communication failure as well as to a security breach.
SMS provides a secure and reliable alternative to email, while also complementing the easy use of email. Without SMS, you’re flying solo with email—every service you use probably requires an email address, and all security precautions can become undone if someone unwanted gets access.
Keep the second link in your chain secure—work with the right SMS software and hardware.
Hackers can get a hold of your passwords easily through your mobile provider without the right security precautions.
Reliance on a secure SMS gateway ensures your communications stay up and running through SMS, even when internet is down. The right SMS gateway will keep your information secure through the two-factor authentication process and support your business in the event of an internet disruption.
Naturally, both users and businesses want their methods of communication to be calm and dependable.
SMSEagle hardware SMS gateways send SMS messages directly to 3G network without using Internet connection. The gateway will work even if Internet connection fails. The SMSEagle gateway, once purchased, is located in your company premises. These assures you control over security and confidentiality of SMS communication. No matter the temperature or humidity conditions the hardware sticks with you.
If you care about quality and security, you need a reliable SMS gateway solution to ensure that your mobile carrier isn’t the weakest link in your security chain.